The Complete Guide to Vetting and Hiring Information Security Consulting Firms
Finding the right information security consulting firm requires a clear, efficient way to vet and compare providers based on specific technical and business requirements. The wrong partner can lead to misaligned strategies, budget overruns, and critical security gaps. This is especially true for leaders in regulated industries or those managing complex multi-cloud environments.
This guide eliminates the guesswork. Instead of a subjective list of firms, we focus on the most effective platforms and directories where you can find and evaluate partners. We cut through the marketing hype to show you where to look for certified, peer-reviewed, and platform-specific security experts. For each resource, you’ll find a direct link, its unique value, and how to use its search and filter functions to your advantage.
You will learn how to:
- Identify consulting partners with verified AWS, Azure, or Google Cloud competencies.
- Access peer reviews from other enterprise and mid-market buyers.
- Find accredited penetration testing and incident response firms through industry bodies like CREST.
- Effectively compare specialists in threat intelligence, compliance, and application security.
This is a curated roundup for CIOs, CTOs, and security leaders who need actionable intelligence, not just another list. Let’s dive into the definitive resources for finding your next information security consulting partner.
What is information security consulting and why do you need it?
Information security consulting provides expert guidance to protect your organization’s digital assets from cyber threats. You need an info-sec consultant to navigate complex compliance frameworks, identify hidden vulnerabilities, and implement scalable security architectures that internal teams often lack the time or specialized skills to build.
Cyber threats are evolving faster than most internal IT teams can adapt. A specialized consulting firm brings threat intelligence from the front lines, ensuring your defenses are aligned with the latest attack vectors rather than relying on outdated perimeter security models.
What are the core services offered by top security consulting firms?
Top information security consulting firms offer services that include penetration testing, compliance auditing (like SOC 2 and HIPAA), incident response planning, and cloud security architecture. They transition organizations from reactive defense to proactive, resilient security postures.
These firms often act as a virtual Chief Information Security Officer (vCISO), providing strategic leadership off-the-shelf. Their value is most apparent in complex, multi-cloud environments where misconfigurations—not sophisticated nation-state hackers—are the leading cause of data breaches.
How much do information security consulting services typically cost?
Information security consulting services typically cost between $175 and $400 per hour. Specialized engagements like elite penetration testing or emergency incident response command higher rates, while routine compliance governance may be less expensive.
To provide a clearer picture, here is a general breakdown of InfoSec consulting costs based on firm size and expertise:
| Firm Category | Typical Hourly Rate | Project Minimum | Best Fit For |
|---|---|---|---|
| Independent Security Researchers | $150 - $250 | $10,000 | Targeted vulnerability assessments, specific app sec reviews |
| Boutique Cybersecurity Firms | $200 - $350 | $30,000 | Penetration testing, SOC 2 / ISO 27001 readiness, cloud architecture |
| Mid-Market MSSPs & Consultancies | $250 - $400 | $75,000 | Comprehensive vCISO services, 24/7 monitoring, end-to-end compliance |
| Top-Tier Global Integrators | $350 - $600+ | $300,000 | Multinational enterprise risk management and board-level security strategy |
Key Insight: The cost of a breach far exceeds the cost of a proactive consulting engagement. When evaluating fees, factor in the financial risk of non-compliance, reputational damage, and operational downtime that the firm is helping you avoid.
Where are the best places to find top information security consulting firms?
The best places to find top information security consulting firms are specialized directories like CloudConsultingFirms.com, review platforms like Gartner Peer Insights, and cloud-provider networks like the AWS Security Competency program. These platforms provide verified data for vendor vetting.
1. CloudConsultingFirms.com
CloudConsultingFirms.com is a data-driven guide for shortlisting and vetting information security consulting firms that specialize in AWS, Azure, and Google Cloud environments. Its primary function is to equip technology leaders with evidence-based insights to make informed partnership decisions, cutting through marketing noise to focus on verified performance.
The platform distinguishes itself with a rigorous, methodology-backed approach to ranking and profiling cloud partners. Its rankings are built on an aggregation of over 2,400 verified client reviews, partner certifications, documented project outcomes, and team size. This allows buyers to quickly assess a firm’s demonstrated capabilities and market reputation.
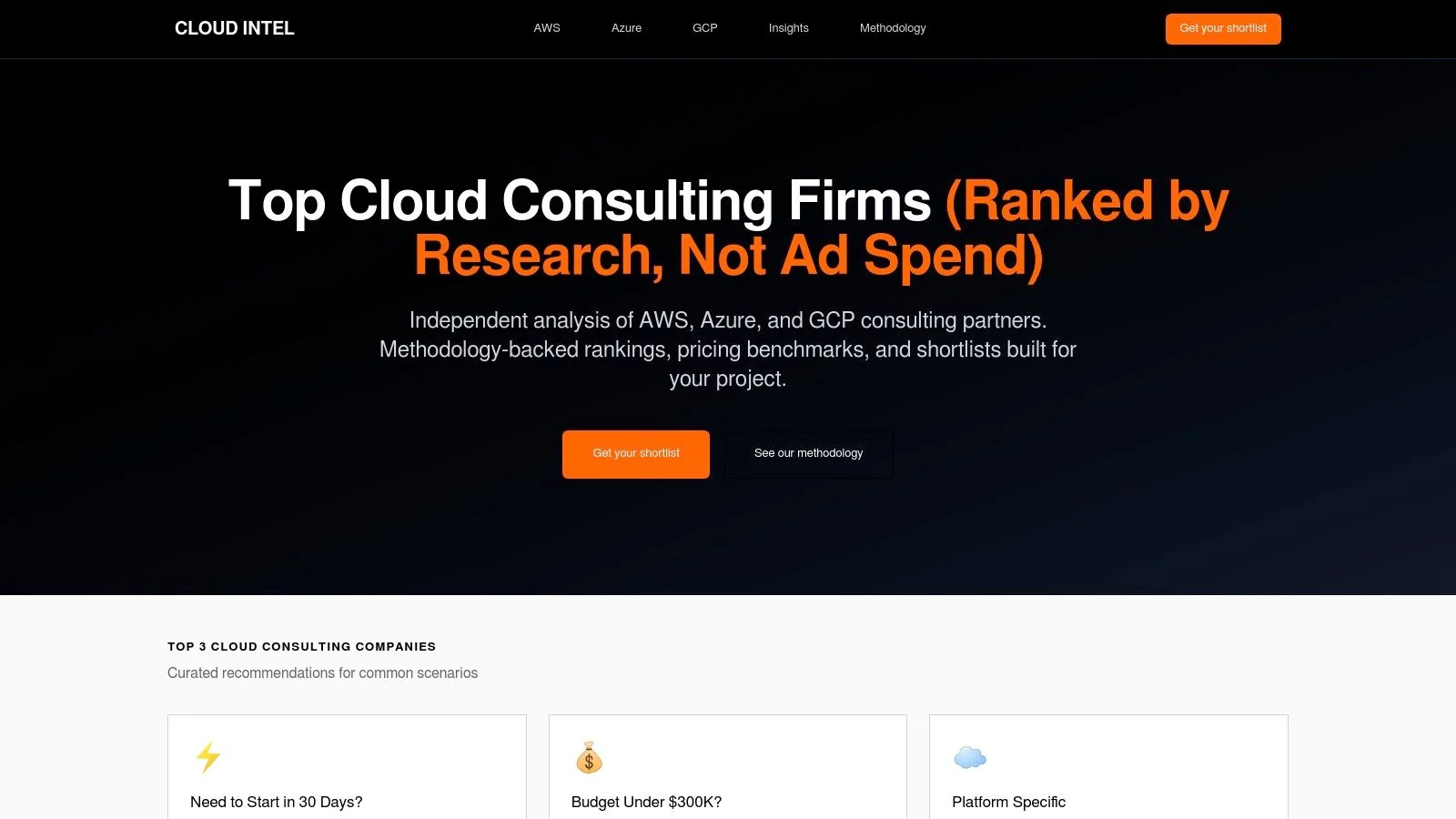
Key Features and Decision-Making Tools
CloudConsultingFirms.com offers a suite of practical tools designed to accelerate the vendor selection process. These features are particularly useful for teams needing to align technical requirements with budget and compliance constraints.
- Interactive Shortlist Workflow: A 3-question interactive quiz generates a tailored shortlist of potential partners in minutes. This tool helps narrow the field based on your primary cloud platform (AWS, Azure, GCP), project scope, and budget.
- Transparent Pricing Benchmarks: The platform provides rare transparency into typical project costs, listing firm-specific rate ranges. For example, it shows estimates like Mission Cloud (
$100K+), Caylent ($200K+), and Slalom (~$250K+), enabling teams to set realistic budget expectations. - Data-Driven Partner Signals: Profiles are enriched with crucial partner-level details, including AWS/Azure/GCP Premier and Advanced designations, documented industry specializations (like healthcare, fintech, retail), and explicit compliance capabilities (such as HIPAA, PCI-DSS, SOC 2).
- Practical Calculators and Alerts: The site includes an ROI calculator to help build a business case and “red-flag alerts” that surface potential risks, such as a mismatch between a firm’s stated expertise and its documented project history.
Why It Stands Out
In a market saturated with sponsored content, CloudConsultingFirms.com’s commitment to independent, evidence-based rankings is its core strength. The scoring methodology heavily weights objective criteria such as certifications, client feedback, specialization, and post-migration support. Top-ranked firms like Slalom (9.2/10) and Caylent (9/10) are presented with clear scores, providing immediate social proof. This approach empowers buyers to prioritize partners with proven track records.
The platform is free to use for buyers. It maintains its independence by clearly labeling any paid or featured placements, ensuring users can distinguish between organic rankings and sponsored profiles. While the directory provides a wealth of pre-vetted information, it is a starting point, not a substitute for formal RFP processes and due diligence. For those new to this ecosystem, the site offers foundational knowledge; you can learn more about the fundamentals of cloud consulting on CloudConsultingFirms.com.
Pros and Cons
| Strengths (Pros) | Weaknesses (Cons) |
|---|---|
| Independent, Methodology-Backed Rankings: Prioritizes evidence (certifications, reviews, outcomes) over ad spend for unbiased vendor comparisons. | Not a Substitute for Formal Vetting: Buyers must still conduct their own RFPs, reference checks, and contract reviews to validate a firm’s claims. |
| Comprehensive Data and Social Proof: Aggregates 2,400+ verified reviews and partner signals across AWS, Azure, and GCP, offering deep insights. | Potential for Underrepresentation: The platform’s focus on visible, larger partners may result in smaller or hyper-niche providers being underrepresented. |
| Practical Decision Tools: An interactive quiz, ROI calculator, and clear budget tiers streamline the shortlisting process. | Paid Placements Exist: While clearly labeled, users should critically evaluate both sponsored and organically ranked firms. |
| Transparent Pricing Benchmarks: Publishes firm-level rate ranges, helping organizations set realistic budgets. | |
| Quarterly Updates and Partner Signals: Keeps information fresh, highlighting key details like industry strengths and compliance expertise. |
Best For: CIOs, CTOs, and procurement teams in mid-market and enterprise organizations seeking a data-driven, efficient way to identify and shortlist top-tier information security consulting firms specializing in AWS, Azure, or GCP.
2. Clutch – Cybersecurity Consulting Directory
Clutch is a B2B marketplace for identifying and vetting information security consulting firms. It operates as a comprehensive directory, aggregating verified client reviews, detailed service descriptions, and company profiles to facilitate side-by-side comparisons. This platform is particularly valuable for building an initial shortlist of potential partners.
It simplifies the discovery process by allowing users to filter vendors by specific cybersecurity needs like penetration testing, governance, risk, and compliance (GRC), or incident response. Its location-based filters, which can narrow results to the US or specific metro areas, are a significant advantage for organizations with regional requirements.
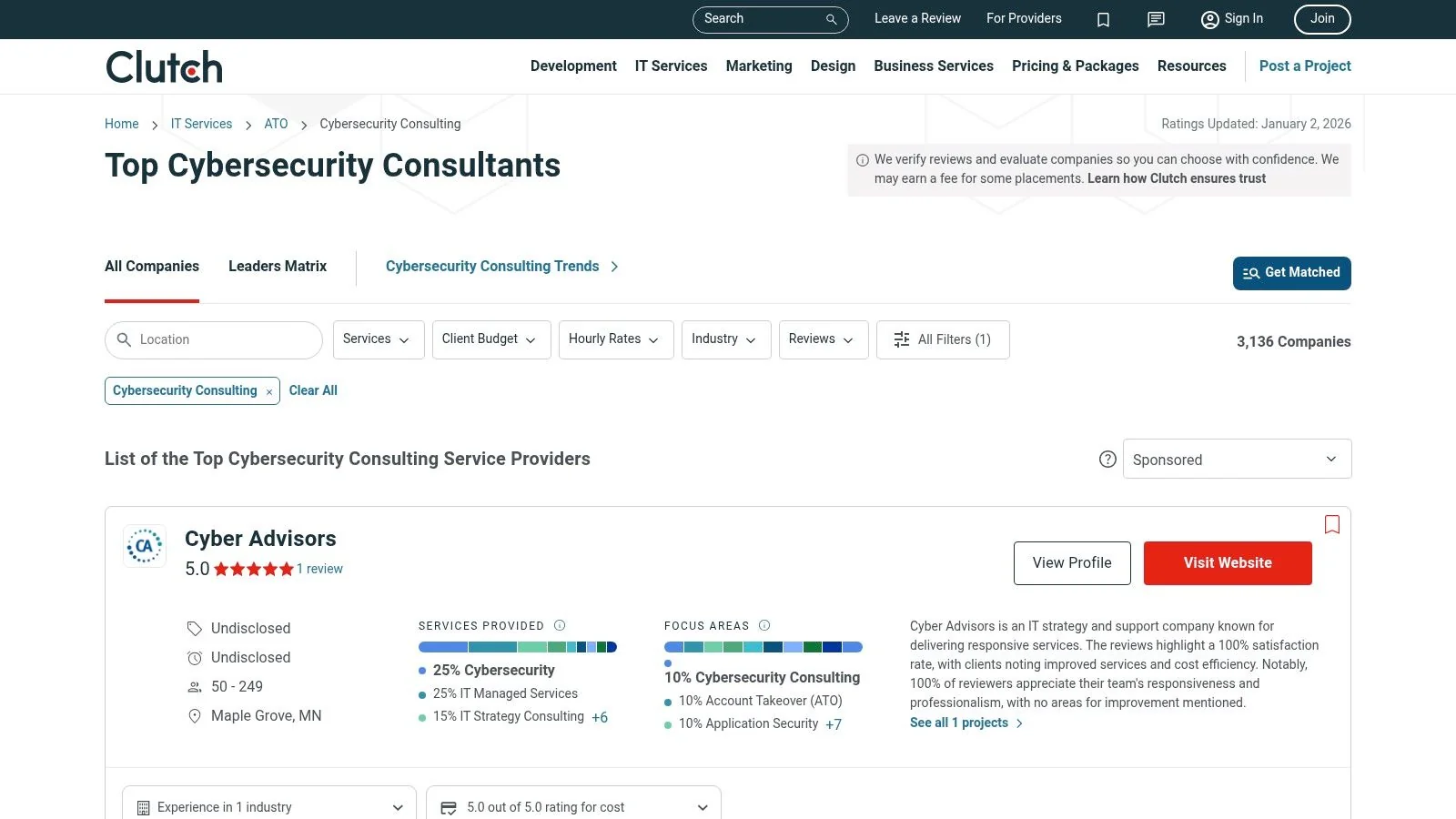
Key Features and User Experience
What sets Clutch apart is its commitment to verified reviews. Each review is conducted through a phone interview or a detailed online form with a former client, adding a layer of authenticity. This firsthand feedback provides insights into a firm’s communication style, project management capabilities, and ultimate impact.
The platform’s user interface is designed for efficient comparison. Key features include:
- The Leaders Matrix: This tool plots firms based on their ability to deliver and their focus on specific services, offering a visual shortcut to identify top-tier providers.
- Transparent Pricing Cues: Many profiles include typical hourly rates (e.g., $150-$199/hr) and minimum project sizes (e.g., $25,000+), which are critical for aligning potential partners with budget constraints.
- Saved Shortlists: Users can save and compare profiles, streamlining the RFP and due diligence phases.
Pros and Cons
| Pros | Cons |
|---|---|
| Deep directory of security-specific firms with detailed portfolios and industry specializations. | Sponsored listings can appear alongside organic results, requiring users to distinguish between them. |
| Verified, recent client reviews provide credible, up-to-date insights for procurement decisions. | Data consistency varies; some vendor profiles lack complete pricing information or detailed case studies. |
| Granular filtering by location, budget, and service line streamlines the vendor discovery process. | The sheer number of firms can be overwhelming without applying precise filters. |
Website: https://clutch.co/it-services/cybersecurity/consulting
3. Gartner Peer Insights – Security Consulting Services, Worldwide
Gartner Peer Insights is a B2B review platform backed by the authority of the technology research firm. It serves as a critical due diligence tool for enterprise buyers needing to evaluate information security consulting firms based on validated end-user experiences. Its reviews undergo a strict verification process, ensuring that feedback comes exclusively from legitimate clients.
This platform is powerful for comparing major consultancies and specialized providers on a global scale. It allows technology leaders to assess firms based on satisfaction scores across various capabilities, from security strategy and technical consulting to incident response and managed security services. For organizations where compliance and enterprise-grade validation are paramount, Gartner Peer Insights provides an essential layer of trusted validation.
Key Features and User Experience
The core value of Gartner Peer Insights lies in its rigorous, multi-step review validation process, which confirms the reviewer’s identity, role, and relationship with the vendor. This enterprise-grade verification builds a high level of trust in the platform’s ratings and qualitative feedback, making it an indispensable resource for risk-averse decision-makers.
Key features that facilitate the selection process include:
- Dedicated Security Consulting Category: The platform organizes vendors into a specific “Security Consulting Services, Worldwide” market, allowing for direct, apples-to-apples comparisons.
- Enterprise-Grade Filtering: Users can filter reviews and vendors by company size, industry, and deployment region, helping to identify consultants with proven experience in similar environments.
- Provider Comparisons: The interface allows for side-by-side analysis of vendors, highlighting overall ratings, willingness to recommend, and detailed feedback on specific service capabilities.
Pros and Cons
| Pros | Cons |
|---|---|
| Trusted review rigor is highly suitable for large enterprises and regulated industries (e.g., finance, healthcare). | Review coverage can be inconsistent; some niche or newer firms may have very few reviews. |
| Provides strong signals on firms known for complex work like FedRAMP, incident response, or security strategy. | While reviews are free to access, full integration with Gartner’s analyst research requires a paid subscription. |
| Verified, enterprise-level reviews offer a high degree of confidence in the feedback’s authenticity. | The platform’s focus is primarily on established, larger consultancies, with less visibility for smaller boutiques. |
Website: https://www.gartner.com/reviews/market/security-consulting-services-worldwide
4. AWS Security Competency Partners – Partner Solutions Finder
For organizations invested in the Amazon Web Services ecosystem, the AWS Partner Solutions Finder is an indispensable resource for locating vetted information security consulting firms. This platform is an official, curated directory of partners who have achieved the AWS Security Competency. This designation is only awarded to firms that demonstrate significant technical proficiency and proven customer success in securing AWS environments.
This platform is the ideal starting point for businesses standardizing on AWS. It allows users to filter for partners specializing in critical domains such as Identity and Access Management (IAM), Threat Detection and Response, Infrastructure Security, and Data Protection. This targeted approach ensures that organizations can quickly identify consultants with verified expertise specific to their cloud security challenges.
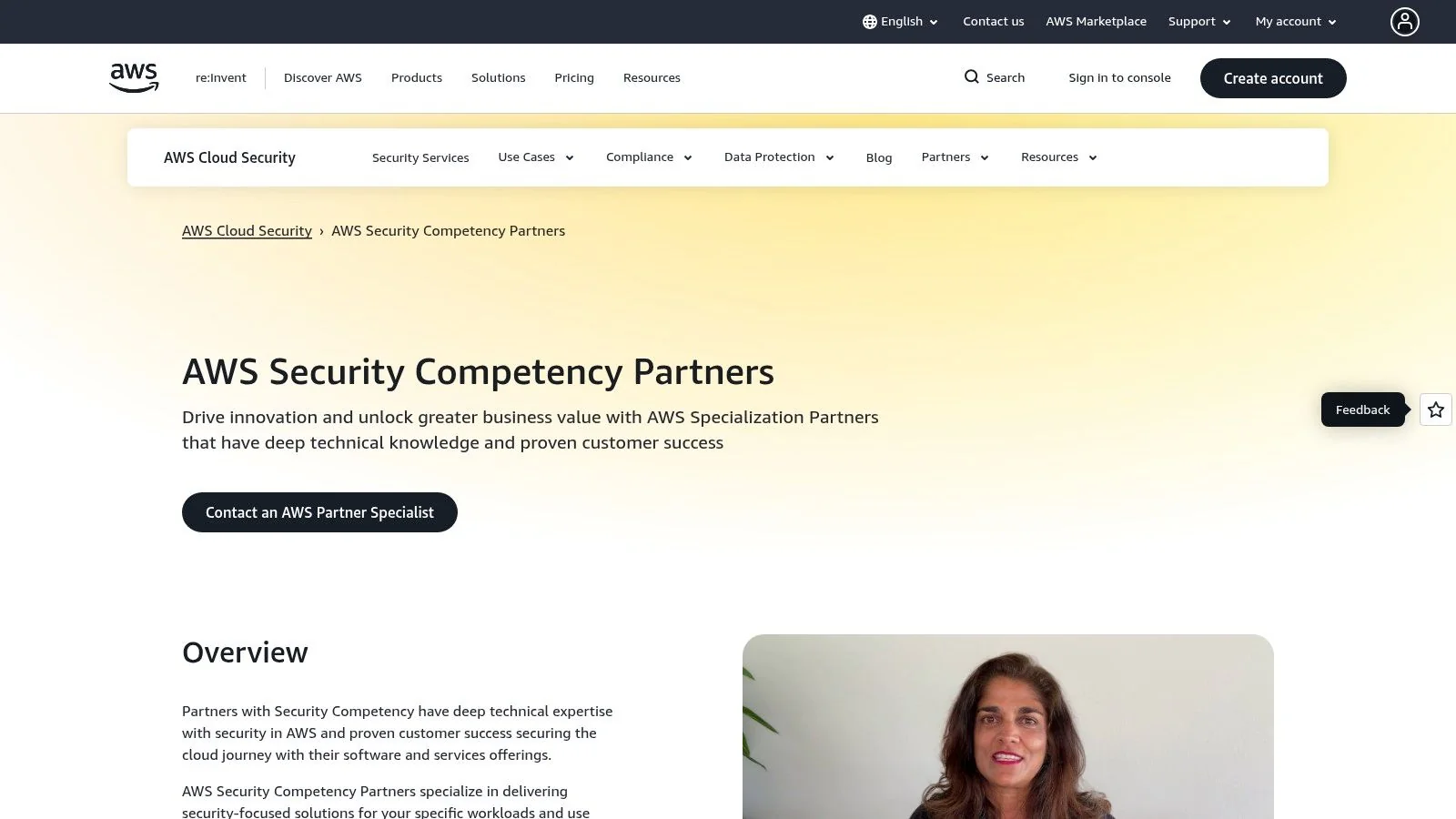
Key Features and User Experience
The primary value of the AWS Security Competency program is its rigorous validation process. Partners must pass a demanding third-party audit of their security practices and technical capabilities. This pre-vetting significantly de-risks the procurement process for AWS customers.
The platform is designed to connect customers with the right expertise efficiently. Key features include:
- Security Competency Categories: Users can filter partners based on specific security use cases, such as Application Security, Compliance and Privacy, or Infrastructure Security, ensuring a precise match for project needs.
- Detailed Partner Profiles: Each listing provides an overview of the partner’s offerings, office locations, and links to customer success stories and case studies. For those in regulated industries like healthcare, finding partners with specific expertise is critical. You can learn more about HIPAA compliance in the cloud to understand the importance of specialized partners.
- Direct Engagement Workflow: The platform facilitates direct contact with partners, streamlining the initial stages of the procurement process.
Pros and Cons
| Pros | Cons |
|---|---|
| High-signal, third-party validation reduces partner selection risk for critical AWS security programs. | Primarily AWS-centric, making it less useful for multi-cloud or on-premises security initiatives. |
| Streamlined discovery to surface and engage specialized partners for complex cloud security initiatives. | Detailed information often resides on the partner’s own website, requiring extra navigation to compare firms. |
| Curated lists of partners with proven customer success and deep technical expertise in specific AWS services. | The focus is on technical competency, so buyers may need to conduct separate due diligence on cultural fit. |
Website: https://aws.amazon.com/security/partner-solutions/
5. Microsoft Azure Marketplace / AppSource – Security Consulting Services
Microsoft’s dual marketplaces, Azure Marketplace and AppSource, offer a productized approach for engaging with information security consulting firms. Instead of open-ended proposals, these platforms list pre-scoped consulting services, often focused on the Microsoft ecosystem. This model is ideal for teams needing specific, time-boxed engagements like security assessments or threat modeling workshops with clear deliverables and predictable costs.
This platform is valuable for organizations invested in Azure and Microsoft 365. It streamlines the procurement of pilot projects or targeted remediation efforts, allowing security leaders to quickly engage certified partners for well-defined tasks. The marketplace acts as a direct channel to vendors with proven expertise within the Microsoft stack.
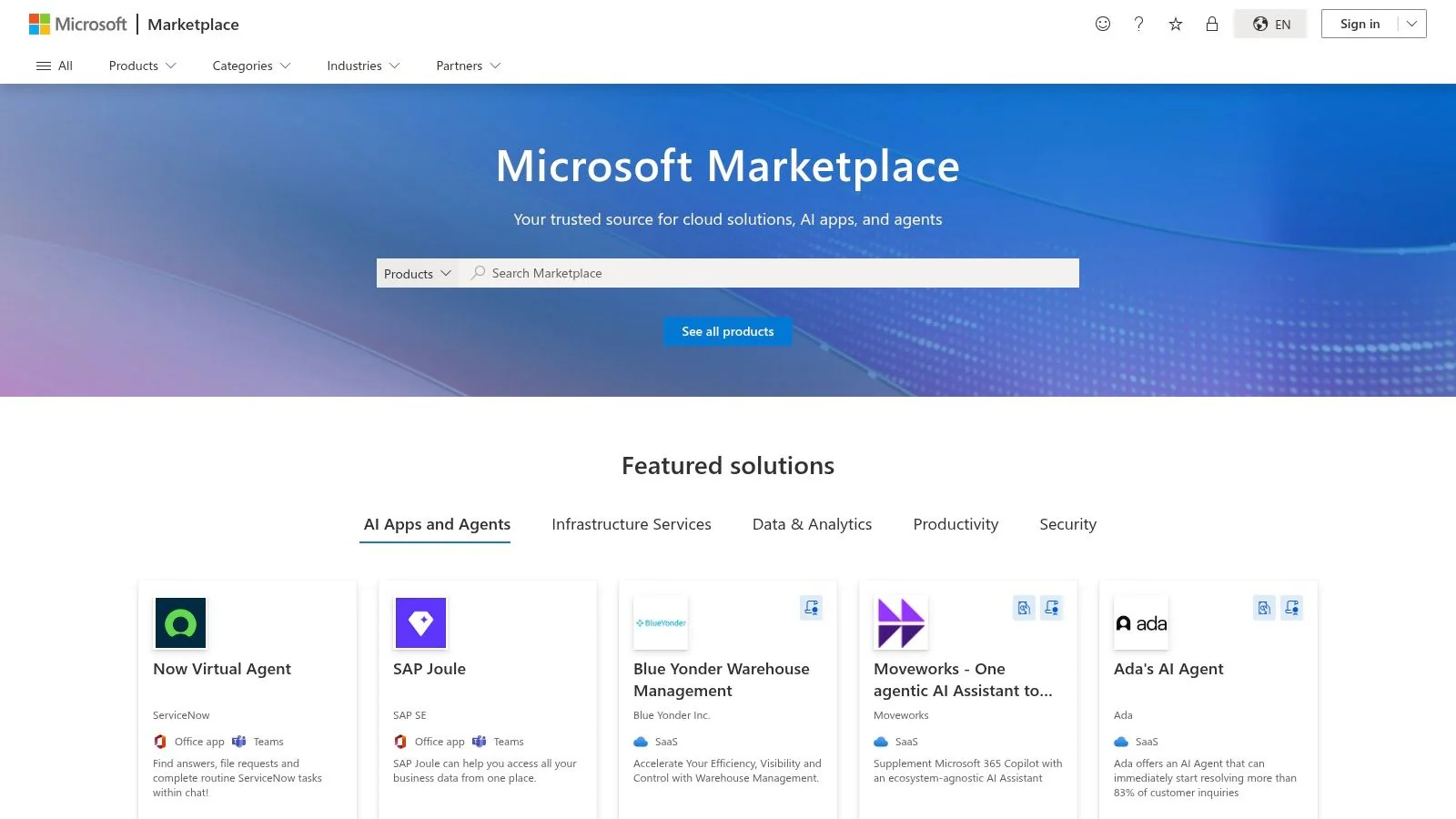
Key Features and User Experience
The standout feature of the Microsoft marketplaces is the prevalence of pre-packaged consulting offers. These listings often function like products, complete with a defined scope, timeline, deliverables, and a starting price. This transparency simplifies budgeting and accelerates the procurement cycle for tactical security initiatives.
The user experience is designed for rapid engagement with Microsoft technologies. Key features include:
- Fixed-Scope Offers: Many services are listed as fixed-term engagements (e.g., “4-Week Security Assessment” or “2-Day Threat Modeling Workshop”) with explicit outcomes, removing the ambiguity of traditional proposals.
- Microsoft-Certified Partners: The marketplace primarily features Microsoft partners, ensuring a high degree of familiarity with Azure, Sentinel, Defender, and other M365 security tools.
- Streamlined Procurement: The platform integrates vendor contact and transaction mechanics, making it easy to initiate a proof-of-concept or a short-term project directly from the listing.
Pros and Cons
| Pros | Cons |
|---|---|
| Transparent, upfront pricing on many fixed-scope offers enables quick procurement and budget approval. | Strong bias toward the Microsoft stack; less suitable for multi-cloud or non-Microsoft environments. |
| Faster alignment and deployment for proof-of-concepts, workshops, and short-term security engagements. | Complex, strategic programs often require custom SOWs that fall outside the marketplace offers. |
| Direct access to a curated list of Microsoft-vetted and certified security partners. | The focus on pre-scoped offers may not fit organizations with unique or undefined security challenges. |
Website: https://appsource.microsoft.com/
6. Google Cloud – Security Partners and Partner Advantage Directory
For organizations invested in the Google Cloud ecosystem, the Partner Advantage directory is an indispensable tool for locating qualified information security consulting firms. This platform is a curated ecosystem of partners that have been officially vetted and validated by Google for their expertise in securing GCP environments. This alignment is critical for companies looking to protect their cloud-native workloads and ensure compliance specific to Google Cloud services.
The directory helps businesses find partners with specific competencies, ranging from cloud-native security posture management (CSPM) to implementing zero-trust architectures on GCP. By focusing exclusively on partners with proven Google Cloud capabilities, it eliminates the guesswork involved in determining if a generalist firm can handle the nuances of services like BigQuery or Google Kubernetes Engine (GKE).
Key Features and User Experience
What sets the Google Cloud Partner Advantage directory apart is its system of official designations. These are earned credentials that signify a partner’s deep technical knowledge and successful client engagements. This verification provides a high level of confidence for procurement teams.
The platform’s user experience is designed to guide users to the right type of partner. Key features include:
- Specialization and Expertise Badges: Users can filter for partners holding the “Security Specialization,” which is the highest technical designation, or those with specific Expertise in areas like “Cloud Security.”
- MSSP and ISV Distinctions: The directory clearly separates Managed Security Service Providers (MSSPs) for ongoing security operations from Independent Software Vendors (ISVs) that offer security product integrations.
- Direct Capability Mapping: The platform helps users understand how partner designations map to real-world capabilities, such as securing data analytics workloads or deploying Chronicle Security Operations.
Pros and Cons
| Pros | Cons |
|---|---|
| High-trust validation of security capabilities specifically for Google Cloud workloads and services. | The directory UX can route users through multiple pages, making side-by-side comparisons less streamlined. |
| Offers a blend of consulting, managed security options, and ecosystem integrations in one platform. | Primarily GCP-oriented; less applicable for organizations with a heavy presence in AWS or Azure. |
| Partners are vetted by Google, ensuring a baseline of technical proficiency and service quality. | Lacks the transparent, user-generated reviews and pricing cues found on platforms like Clutch. |
Website: https://cloud.google.com/partners
7. CREST Accredited Member Directory
For organizations in highly regulated industries, the CREST Accredited Member Directory serves as a critical due diligence tool. CREST is an international not-for-profit accreditation body that evaluates the capabilities and methodologies of information security consulting firms. Instead of relying on client reviews, it provides a list of companies that have passed rigorous, independent assessments of their technical and operational competence.
This directory is valuable for validating a vendor’s claims in specialized areas like penetration testing, incident response, threat intelligence, and Security Operations Center (SOC) services. Procurement teams can use it to verify that a potential partner adheres to internationally recognized standards, helping to de-risk the selection process for compliance-driven projects.
Key Features and User Experience
The primary value of the CREST directory lies in its function as a mark of quality and trust. The accreditation process is exhaustive, covering company policies, procedures, and the specific skills of individual security professionals. This ensures that listed firms have both technical expertise and corporate governance.
The platform’s interface is straightforward and built for validation. Key features include:
- Accreditation-Based Filtering: Users can search for members based on the exact CREST-accredited service they need, such as Penetration Testing, STAR (Simulated Targeted Attack and Response), or Cyber Security Incident Response.
- Geographic Search: The ability to filter by country allows US-based buyers to quickly identify local or national providers that meet CREST standards.
- Direct Verification: Each listing provides a direct link to the member’s profile, confirming their current accreditation status and the specific services for which they are approved.
Pros and Cons
| Pros | Cons |
|---|---|
| Provides a strong assurance marker for offensive security and incident response providers. | The directory is a listing only; buyers must still contact firms for quotes, references, and proposals. |
| Helps de-risk vendor selection, which is crucial for audits, compliance, and regulated environments. | Not all reputable US firms pursue CREST accreditation, so it should be used alongside other validation tools. |
| Audited methodologies mean firms have proven, consistent, and high-quality QA processes. | The focus is primarily on technical service delivery rather than strategic or GRC consulting. |
Website: https://www.crest-approved.org/members/
Top 7 InfoSec Consulting Directories Comparison
| Provider | Primary focus / scope | Implementation complexity | Resource requirements | Expected outcomes | Ideal use cases | Key advantages |
|---|---|---|---|---|---|---|
| CloudConsultingFirms.com | Independent, data-driven guide for AWS/Azure/GCP consulting partners with rankings and pricing benchmarks | Low for shortlisting; vendor selection requires standard RFP/validation | Minimal to generate shortlist; moderate for validation and procurement | Evidence-based shortlists, pricing ranges, firm comparisons and risk alerts | CIOs/CTOs, procurement teams, regulated enterprises evaluating cloud migration partners | Methodology-backed rankings, ROI tools, transparent pricing and verified reviews |
| Clutch – Cybersecurity Consulting Directory | B2B marketplace of security consulting firms with reviews, filters and leader matrix | Low — search, filter and compare profiles | Low to moderate; profile detail varies by vendor | Shortlists with client reviews, pricing cues and regional filters | Procurement teams shortlisting security vendors by budget and location | Large security vendor coverage, regional filters, side-by-side comparisons |
| Gartner Peer Insights – Security Consulting Services | Analyst-run review platform with enterprise-grade, validated end-user reviews | Low to moderate; enterprise-focused expectations | Low to view reviews; subscription for full analyst research | Validated satisfaction scores and enterprise comparison signals | Regulated and enterprise buyers needing rigorous validation | Strong review validation and trusted enterprise signal |
| AWS Security Competency Partners | AWS-curated partners validated for security competency and customer success | Moderate — engagement optimized for AWS environments | Moderate; assumes AWS stack and possible integration work | Vetted partners for AWS security projects and specialist capabilities | Organizations standardizing on AWS or doing cloud security transformations | Third-party validation tied to AWS programs and category filters |
| Microsoft Azure Marketplace / AppSource | Marketplace of pre-scoped Azure/M35 security consulting offers with stated deliverables and prices | Low for fixed-scope offers; higher for custom programs | Low for pilots/proof-of-concepts; higher for multi-month SOWs | Rapid procurement of assessments, time-boxed engagements and starter pricing | Quick pilots, remediation workshops and Azure/M365-focused work | Transparent entry pricing and streamlined procurement mechanics |
| Google Cloud – Security Partners | GCP partner directory highlighting Security Specialization, MSSPs and integrations | Moderate — GCP-centric partner discovery | Moderate; best for GCP workloads or multicloud with GCP focus | Validated partners and managed security options aligned to GCP | Buyers standardizing on Google Cloud or integrating GCP security | Security specialization badges and ecosystem integration options |
| CREST Accredited Member Directory | Accreditation listing for firms meeting audited standards in pentest, IR, SOC and related services | Low for lookup; selection still requires vendor contact and vetting | Low to identify accredited firms; moderate for procurement and references | Shortlist of independently accredited providers with audited QA and methodologies | Regulated sectors needing assurance for offensive security and IR | Independent accreditation, strong assurance for methodology and QA |
How do you successfully evaluate and select an information security consulting firm?
Successfully evaluate and select an information security consulting firm by analyzing their specific platform competencies, verifying third-party accreditations like CREST, and conducting rigorous reference checks. A structured, evidence-based selection process ensures your partner is qualified to protect your most sensitive data.
You have reviewed the directories, from Gartner Peer Insights to the platform-specific expertise in the AWS and Google Cloud partner networks. The right partner is a strategic extension of your team. Your selection process must be as rigorous as the security frameworks these firms will help you implement.
This article has equipped you with a structured approach. We’ve emphasized aligning a firm’s specialization with your organization’s immediate pain points and long-term goals. Remember, a firm celebrated for its Fortune 500 transformations may not offer the agile approach a mid-market business requires.
Synthesizing Your Findings for a Confident Choice
As you move to a final decision, consolidate your research and focus on the factors that truly differentiate one firm from another. The tools and directories provide the raw data; now, you must apply your unique business context to interpret it.
Actionable Next Steps for Final Vetting:
- Revisit Your RFP with a Critical Eye: Review your Request for Proposal against the insights gained. Did you specify your technical environment (e.g., multi-cloud, serverless)? Have you clearly articulated your compliance needs (e.g., HIPAA, GDPR, PCI DSS)? A generic RFP invites generic responses.
- Conduct Deep-Dive Reference Checks: Go beyond curated case studies. Ask for references from clients with similar challenges and scale. Ask pointed questions about the project management process, the quality of deliverables, and how the firm handled unexpected challenges.
- Schedule “Chemistry Fit” Interviews: The final candidates should meet with your key internal stakeholders, not just procurement. This includes lead engineers, compliance officers, and relevant business unit leaders. A strong cultural and communicative fit is paramount for a successful partnership.
- Evaluate a Sample Scope of Work (SOW): Request a sample SOW from your top two or three contenders for a small, well-defined project. This exercise reveals their approach to project scoping, resource allocation, and deliverable clarity. It’s a low-risk way to preview their operational rigor.
Key Insight: The best consulting engagement is a collaboration. The firm you choose should not only possess technical mastery but also demonstrate a genuine investment in understanding your business context and a commitment to transparent communication.
Ultimately, your choice will hinge on a triangulation of evidence: the firm’s documented expertise (like those from CREST or AWS), validated client outcomes from sources like Clutch, and the tangible rapport you build during the evaluation process. By following this structured path, you forge a strategic alliance that will fortify your defenses. Your signature on the final contract should be an act of confidence, not a leap of faith.
Ready to accelerate your search and connect with pre-vetted experts? CloudConsultingFirms.com provides a curated directory focused specifically on cloud and information security partners, allowing you to filter by certifications, platform expertise, and industry focus. Visit CloudConsultingFirms.com to streamline your vendor discovery and build your shortlist of qualified information security consulting firms today.
Peter Korpak
Chief Analyst & Founder
Data-driven market researcher with 10+ years helping software agencies and IT organizations make evidence-based decisions. Former market research analyst at Aviva Investors and Credit Suisse. Analyzed 200+ verified cloud projects (migrations, implementations, optimizations) to build Cloud Intel.
Connect on LinkedInContinue Reading
Security
Resources for vetting information security consulting firms
Solving Modern Cloud Compliance Challenges
A technical guide to overcoming modern cloud compliance challenges. Learn to mitigate risks for GDPR, HIPAA, and PCI DSS in complex cloud environments.
10 Actionable Cloud Security Best Practices for 2026
Cut through the noise. Discover 10 technical, actionable cloud security best practices for 2026 covering IAM, encryption, and zero-trust networking.
Stay ahead of cloud consulting
Quarterly rankings, pricing benchmarks, and new research — delivered to your inbox.
No spam. Unsubscribe anytime.